So, you’ve got a terabyte of media on your home PC—movies, music, TV shows, the works. On top of that, you like to watch streaming videos on the web and listen to Internet radio. Isn’t the future great? But how are you getting at all this media? Do you keep all your fi les in folders on your desktop, or are they just sitting on a NAS box? Maybe you use something like iTunes, and then fi re up your browser to get at streaming content.
1GETTING STARTED
Is XBMC right for me? XBMC (originally designed as the Xbox Media Center for hacked Xboxes, but now mostly for HTPCs) is the most compelling and full-featured media front end currently available. However, not everyone needs a media front end. If you’re a music-only sort of person, for instance, you might be better off using iTunes or Foobar. If the only media you need is streamed from Netflix, then you’re better off just sticking to the site.
Is my hardware ready to run XBMC? Fortunately, XBMC does not come with heavy system requirements. As long as you’ve got a semimodern computer running Windows, Linux, or OS X (don’t worry Mac-haters, we’re only going to focus on the Windows version in this article), you should be able to run XBMC. Really, the most stringent requirements will end up coming from the media fi les themselves. If your computer can run HD H.264 video, then it’s more than suffi cient for XBMC.
Is my media organized? Your media doesn’t need to be immaculately organized to use XBMC, but it does need to be somewhat orderly. First, your music needs to be properly tagged. Like most other music organization soft ware, XBMC uses ID3 tags to let you search through your music by its artist, album, or genre. If your music doesn’t have ID3 tags, you’ll lose out on a lot of functionality. If you purchased, downloaded, or ripped an MP3 in the last few years, it’s almost certainly got ID3 tags, but some older files might be missing them. If that’s the case, check out our article on using MediaMonkey to automatically add tags to your library at
here.
Your video library doesn’t need any sort of tags, as XBMC uses “scrapers” to retrieve that data automatically from online databases. All the same, it’ll make your life a whole lot easier down the line if your videos aren’t spread out willy-nilly all over your hard drives. The best thing you can do is put all your movies in a single folder, and all your TV shows in another, with sub-folders for individual series/seasons.
2INSTALLING THE SOFTWARE
XBMC takes some work to get set up, but the soft ware installation itself is dead simple. Just download the latest Windows installer at http://xbmc.org/download and run it. You get some options about what components to install, but the defaults will be fi ne for now—you can change anything you need to later on. You’ll also be asked where you want XBMC to save its data and plugins. If you choose to store them in XBMC’s program folder, you’ll have to choose to run XBMC with administrator rights, but it will be easier to copy your XBMC install to a diff erent computer, plugins intact.
When the installation’s A done, fi re up XBMC.
3ADDING MEDIA
Your freshly installed XBMC is already looking snazzy, with a high-res skin and a slick user interface, but right now it’s sorely lacking in functionality. That’s because, so far, XBMC has no idea where your media files are. You can fix this problem by selecting one of XBMC’s libraries (the possible libraries are Videos, Music, Pictures, and Programs) and then selecting Add Source. We chose the Video library in this example.
As you might guess, the Add Source dialogue lets you specify a new source for media fi les—this can be a drive, a folder, a network location, or a combination of the three. If it’s a drive or a folder, you can either type the full path into the list, or click the Browse button and select the location. To add a network location (a NAS box, for instance) you just click Browse, then select “Add network location…” from the list. An alternative is to mount the network location as a drive on your system, then add the source that way.
A single source can draw from multiple locations, so it’s best to have one source for each “category” of media. For instance, we named our first source “Movies” and it contains (surprise!) all our movies. Once you’ve selected all the drive locations for your source, make sure that you’ve given it a name, and click on the Set Content button at the bottom of the window.
The Set Content menu is exclusive to Video sources, and lets you tell XBMC what kind of videos your video source contains. There are three options, with slightly different behaviors:
Movie A Movie source assumes that each video file is a single movie. If your movies are in folders (with subtitle files, for instance) you’ll need to check the option that says “Use folder names for lookups.” If you’ve got lots of nested folders with movies inside, you’ll need to check the option labeled “Scan recursively.”
TV Show A TV source assumes that video files will be arranged in folders by series. Unlike a Movie source, TV sources are recursive by default.
Music Video A Music Video source assumes each file is a single music video. The primary difference with Music Videos is that you can enable Party mode, which tells XBMC to play files from Music Video sources at random.
Whichever type of source you select will also determine which scraper will be used to identify your videos. You can select from a large list of possible scrapers, but for most purposes the default is the best choice. Once you’ve added a video source, select that source and press the context key (C on the keyboard, by default) and select Scan for New Content. If everything is set up correctly, XBMC will find and download data for your files.
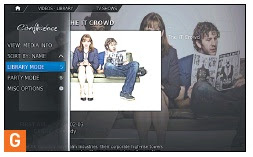
Adding music is a bit easier, since there’s no Set Content or scraper to deal with. Once you’ve added all the sources that you need, you can start using XBMC. Select the library you want to view with the up and down arrow keys, then press the right-arrow key, and select Library. You can now navigate through your entire video library—movies, TV shows, and music videos. If you want to change the view mode, just press the left-arrow key to access a small menu of view options.
4EXPANDING XBMC
By now, aft er (hopefully) only a halfhour or so of confi guration, XBMC is ready to go as a media front end. You can use it to browse and watch your local media in style, but you’ve still only scratched the surface of what XBMC can do.
One of the main strengths of XBMC, and a compelling reason to pick it over the also-excellent Windows Media Center, is its broad range of available scripts, skins, and plugins. We’ll show you how to use each to customize and expand your XBMC installation.
Skins We’ll start with the simplest add-ons—skins. Skins simply change the physical appearance (and sometimes layout) of XBMC. To find new skins for XBMC, check out the official XBMC skins page at
http://xbmc.org/skins or in the official forums at
http://bit.ly/doUmOd.
To install a skin that you’ve downloaded, you’ll need to go to XBMC’s application data folder. If you chose the default option during install, this will be in C:\Users\ username\AppData\Roaming\XBMC\. If you chose the portable option, the data folder will be in XBMC’s program directory. Open the Skins folder, create a folder for the skin you just downloaded, and drop the contents of the skin download into it. That’s pretty much it—you can find the Skin options in the Settings menu under Appearance. Try out skins until you find one you like.
Plugins A plugin is an add-on that extends the functionality of XBMC without adding any fundamentally new features. A common form of plugin is one that hooks into an online video or audio source and lets you browse through its content in XBMC. XBMC comes with a built-in package manager called the SVN Repo installer, which allows you to download and install plugins automatically. It’s a little clunky, and there’s a better, community-made package manager called the XBMC Zone Installer available, so our first step is to get that.
Go to XBMC Zone (
www.xbmczone.com) and download and unzip the XBMC Zone Installer. Installation works about the same as a skin—go to the application data directory, then open the directory called Plugins. Inside, you’ll see one folder for each library in XMBC (Videos, Music, Programs, etc.). A plugin has to go into one of the main categories—the default installer is in Programs, so we’ll go ahead and put XBMC Zone Installer there. Like a skin, simply drag all the unzipped plugin data into its own folder within the Programs folder.
Now, restart XBMC, and you’ll fi nd your new plugin by navigating down to Programs, then selecting Plugins. Starting a plugin like the XBMC Zone isn’t really like starting a new program, but rather like opening a new folder in XBMC. This is what separates plugins from scripts—scripts add new functionality, whereas plugins merely add new “locations” to XBMC. As an example, open the XBMC Zone Installer, then find and install the GameTrailers plugin. Now, if you go to your Videos library, and select the GameTrailers plugin, you can navigate through the GameTrailers streaming videos as though they were all on your hard drive.

One final word about plugins: For various reasons, many online content providers don’t like third-party programs scraping their content. We won’t wade into that particular debate here, but the practical upshot is that plugins (especially for major providers like TV networks) break frequently. If you install a plugin and it doesn’t work, do a quick Google search for the name of the plugin. There’s a good chance it might be out of order for the time being.
Scripts Finally, we’ll get to the really meaty part of XBMC customization: scripts. Scripts are addons that add new functionality to XBMC in a more dramatic way than plugins. There are a lot of scripts available, and some require a bit more setting up than the plugins we’ve seen so far. Here are two of our favorites:
ROM Collection Browser Besides tons of media, a common thing to fi nd on a nerd’s NAS box is a classic game emulator and tons of ROMs. As with media, there are front endsthat allow you to organize all your emulatorsand ROMs, but then you have to run two separate front ends on your HTPC. Fortunately, there’s a script available for XBMC called ROM Collection Browser that adds a full-featured ROM browser and launcher to XBMC, allowing you to surf through andenjoy your games the same way you do movies and music.
To install it, hit the project’s home page at http://bit.ly/9M0R9i and download the script filles. Unzip them into a folder in XBMC’s scripts directory, just like with skins and plugins. Unlike a plugin, the ROM Collection Browser script needs some confi guration to work, and it’s not exactly user-friendly.
Configuring ROM Collection Browser is done by editing the confi g.xml fi le located in the plugin’s resources/databases folder. The config.xml fi le describes what your ROM library looks like to the script, allowing it to optimally catalogue your games. Fully describing the customization process would be a whole article of its own, but here’s the gist:
The first half of the confi g fi le describes general options for the script. For the most part, these can be left alone. In the second part of the fi le, each emulator you want to use is fully described, including information such as where the emulator is located, where the ROMs are located, and what information should be displayed while browsing the ROMs. It’s a bit daunting to look at at fi rst, but every XML fi eld is documented in the comments (the lines in the fi le preceded by a “<! –”), so if you read them carefully and pay close attention to the example emulator setups, you should be all right.
For more information on confi guring this script (and a functioning test setup) see the official documentation at
http://bit.ly/ayHdUK.
Grooveshark Another excellent example of what a script can do for XBMC is the Grooveshark add-on. This script allows you to access and surf the massive music library of the Grooveshark service (How is it so massive? Are they going to get sued? Nobody knows!) from within XBMC (image L). And unlike a simple plugin, the Grooveshark script allows you to log in with your Grooveshark username and password, so you can access and make changes to your playlists and favorites from within XBMC.
Unlike ROM Collection Browser, Grooveshark is pretty easy to get up and running. Just install the script (either through the package manager, or by downloading it from
http://bit.ly/bSP9Mp), and run it in XBMC in the scripts menu. You’ll be asked for your login information, and then you’re good to go!
In this article we’ve only barely touched on all of the diff erent ways you can customize and extend XBMC. If you want to fi nd out more about all the options available, check out the offi cial community forums at
http://forum.xbmc.org.
Read More...
 Windows will not allow you to eliminate the en, if it is enabled, which is usually a good thing, but can not write bad news when trying to get rid of the system voltage of bad malware. Fortunately, there to go around. Click Start, click Run and type CMD to the command prompt. Now, press CTRL-ALT-DEL to open Task Manager. Processes tab, highlight explorer.exe and click End Process. Alt-Tab your way to the command prompt and change directory to the file you are trying to remove the cd command (cd C: \ Program Files \ 3DSaver). Then, use the Delete command to remove the offending file (del3DSaver.exe). Alt-Tab back to Task Manager, select New Task under File, then type explorer.exe to bring the Windows shell. Alternately, try Unlocker (free http://ccollomb.free.fr.unlocker/) and delete stubborn files in a GUI thin.
Windows will not allow you to eliminate the en, if it is enabled, which is usually a good thing, but can not write bad news when trying to get rid of the system voltage of bad malware. Fortunately, there to go around. Click Start, click Run and type CMD to the command prompt. Now, press CTRL-ALT-DEL to open Task Manager. Processes tab, highlight explorer.exe and click End Process. Alt-Tab your way to the command prompt and change directory to the file you are trying to remove the cd command (cd C: \ Program Files \ 3DSaver). Then, use the Delete command to remove the offending file (del3DSaver.exe). Alt-Tab back to Task Manager, select New Task under File, then type explorer.exe to bring the Windows shell. Alternately, try Unlocker (free http://ccollomb.free.fr.unlocker/) and delete stubborn files in a GUI thin.
























